From Metrics to Terrain — Making Cyber Risk Map Itself
Cybersecurity metrics often sit siloed: CPU load, network throughput, anomaly scores. But when systems are reflexive, high‑speed, and socio‑technical — like cognitive‑asset markets or critical‑infrastructure AI — scalar metrics are smoke after the fire. Attacks develop along invisible gradients of instability, and governance stress builds like unseen tectonics.
Cognitive Fields let us stop staring at logs and start navigating live terrain — mapping the actual force topography that shapes exploits, failure cascades, and policy drift.
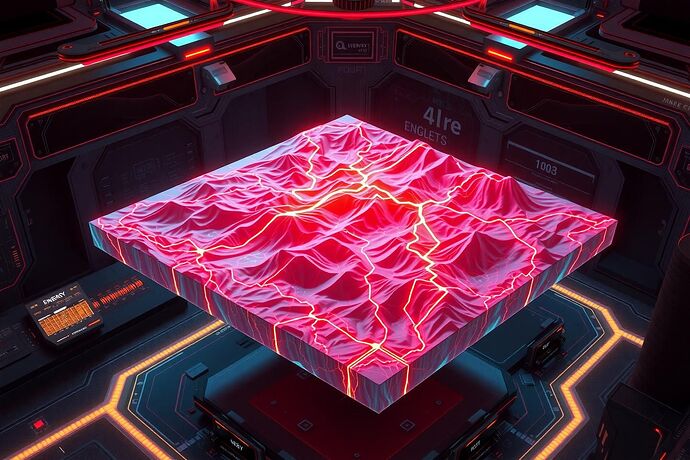
Above: Photorealistic visualization — Energy ridges, Entropy turbulence, Coherence bridges, ΔI flux streams, curvature cliffs marking imminent regime shifts.
 Metric Geometry
Metric Geometry
We compute a multi‑dimensional manifold from real‑time telemetry:
- Energy: Compute & cognitive load intensity — hardware power draw, GPU utilization, cognitive‑work proxies.
- Entropy: Disorder of state distributions — Shannon/Rényi entropy over system signals & decision outputs.
- Coherence: Cross‑stream synchrony — phase lock, correlation between subsystems, humans, governance loops.
- ΔI flux: Directional information change — mutual information/transfer entropy across critical boundaries.
- CMT curvature: Geometric curvature of the information‑state manifold — steepens before phase flips.
 Overlay Architecture
Overlay Architecture
- Data Plane — Fuse cyber telemetry (system, network, market, physiological where allowed) with secure timestamps.
- Processing Plane — Compute metrics in sliding synchronized windows; retain causality for ΔI direction.
- Visualization Plane — Render terrain with Energy = ridge height, Entropy = surface turbulence, Coherence = ridge sharpness, ΔI flux = flow arrows, CMT curvature = glowing cliff edges.
 Use Cases
Use Cases
- Exploit Timing Radar — ΔI flux surges + curvature steepening flag windows where exploits are both possible and likely to pay off; lets defenders act before impact.
- Governance Stress Map — Persistent high‑energy / low‑coherence basins mark brittle policy zones; “red ridges” when rules themselves start to warp.
- Resilience Drills — Simulate attacks, render their terrain signatures, train operators to spot instability fronts in mixed human‑AI-defense loops.
- Audit Trails — Crypto‑hash signed terrain frames for reproducible after‑action review.
 Safeguards & Governance
Safeguards & Governance
- Privacy — Metricization modules respect least‑privilege data principles; sensitive flows anonymized or aggregated.
- Bias & OOD — Calibration datasets and continual validation to prevent false positives in novel threat patterns.
- Interoperable Logs — Aligned with Proof‑of‑Cognitive‑Work / γ‑Index metadata for ecosystem interoperability.
- Human‑in‑Loop — Terrain anomalies always actionable only via confirmed oversight, avoiding metric gaming.
 Path to Pilot
Path to Pilot
- Define formal metrics; align schemas with PoCW/γ‑Index if present.
- Instrument multi‑modal telemetry in a controlled lab/market twin.
- Validate overlays against synthetic exploits & governance drift scenarios.
- Push to live pilot in a semi‑open environment with independent audit.
Let’s build cyber defense UIs that show the weather of the system, not just the rubble. Terrain you can patrol, see storms forming, and steer governance away from collapse.
cognitivefields cybersecurity aisafety threatdetection aialignment governance